Senior Elijah Bouma-Sims ’21 published his first co-authored paper earlier this year, the culmination of an 11-month study on robocalling. First, it won the Distinguished Paper Award at the 29th USENIX Security Symposium. Then it won the first-place Internet Defense Prize, a $100,000 grant that will support future research at NC State.

“Winning the prize was totally unexpected,” Bouma-Sims shares. He says the award will help set up for future projects. “As a first publication, it’s an amazing launch pad to the future. It’s also a little scary because it means that I’m starting at such a high point that it will be hard to follow up.”
Bouma-Sims is passionate about diversity and accessibility, particularly in relation to security. “I hope to spend my career working to make systems secure for all people from different levels of ability and different backgrounds,” he explains. He plans to enroll in a doctoral program next year, with the ultimate goal of becoming a professor so he can mentor students and do research in “human-centered security.”
Knowing he wanted to pursue research early in his sophomore year, Bouma-Sims started by combing through professor bios to find someone working in security who would be willing to take on a computer engineering student. Bouma-Sims, who is majoring in computer engineering and history, explains that most security researchers come from a computer science background. “I was worried I wouldn’t have enough programming experience to do the work.”
Bouma-Sims reached out to Dr. Brad Reaves, an assistant professor in the Department of Computer Science, and spent a semester on a non-research project before becoming an undergraduate research assistant. Bouma-Sims encourages NC State students to not be afraid to email potential connections. “The worst thing they can do is ignore you, and the possible benefits are amazing,” he shares. “If you’re afraid to send an email, just close your eyes and click send.”
Being named a Park Scholar not only brought Bouma-Sims to NC State, but it also enabled him to focus on research early on in his academic career. “Financially, Park Scholarships gave me a freedom that I would not have had otherwise,” he explains. “In research, that meant I could be an unpaid assistant for a semester and learn the ropes much earlier than I might have otherwise been able to.”
“Research as an undergraduate transformed both my professional and academic goals,” Bouma-Sims says. “I wasn’t certain what I really wanted to do before I got seriously involved in research, but after a year of paid work as a researcher, I didn’t want to do anything else.”
The experience also helped clarify what Bouma-Sims needed to focus on to reach his professional goals. “I originally was doing three majors, but I realized that it wasn’t worth the pain to do that when my third major wasn’t important to my goal of becoming a professional researcher.”
When Dr. Reaves approached him about working on a robocalling study, Bouma-Sims was intrigued by the wide applicability of the study. “This is an issue that affects almost everyone in the U.S. and it related directly to my interest in security without not being too theoretical.”
The project used a honeypot to receive thousands of unsolicited phone calls. It tracked the caller numbers and recorded some of the call audio, which allowed the team to identify and cluster distinct robocalling campaigns by comparing “audio fingerprints” from the recordings. “This technique ultimately should be useful for providers to eliminate spam from unsolicited callers,” Bouma-Sims shares. This was one of dozens of findings from the study.
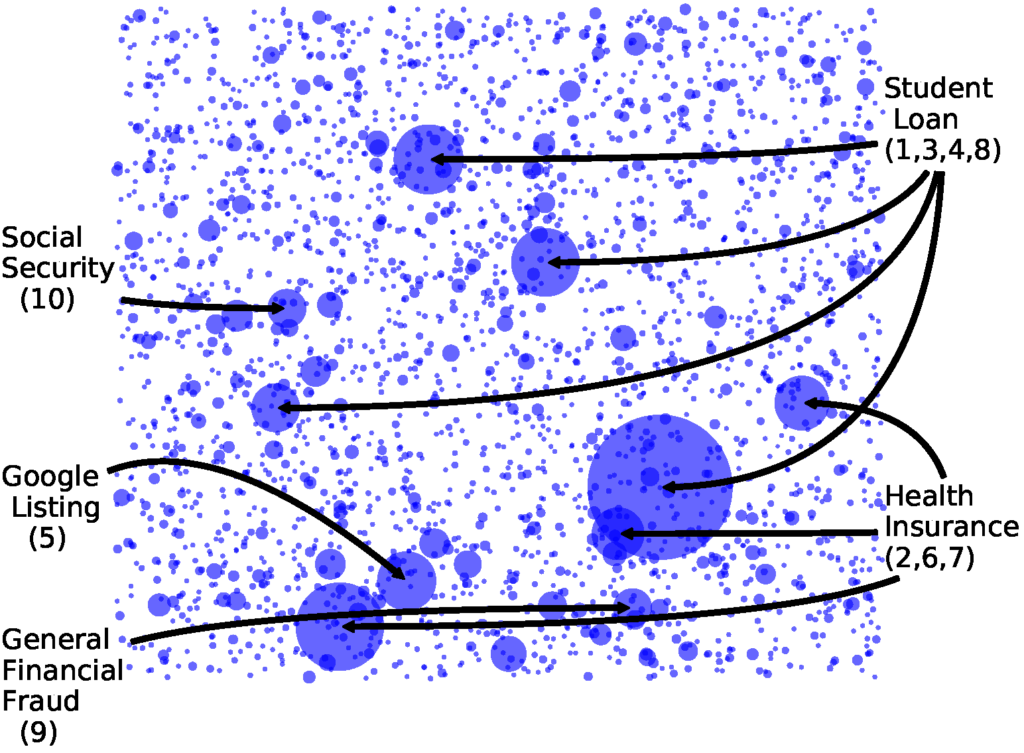
The size of the dot corresponds to the number of calls received.
“The biggest take away for the average person is that you don’t have to fear that answering a robocall will mean you will get more,” Bouma-Sims explains. “You should still be wary of unknown callers, but you don’t necessarily have to reject every call.”
Bouma-Sims was responsible for several aspects of the study’s infrastructure. He worked on programming the “dialplan” to record a random subset of the phone numbers, programming a method of turning raw logs into usable data, and doing speculative research like looking into different methods of call transcription, as well as writing, editing, and creating figures for the paper.
The process of writing the paper involved Bouma-Sims, Dr. Reaves, and lead author Sathvik Prasad isolating themselves in the Wolfpack Security and Privacy Research (WSPR) Lab for two days in a row to write, edit, and re-write.
“It was definitely a crazy two days, but it was a great collaborative process.”
“Who’s Calling? Characterizing Robocalling Campaigns through Audio and Metadata Analysis” is written by Sathvik Prasad, Elijah Bouma-Sims, Athishay Kiran Mylappan, and Brad Reaves and was presented at the USENIX Security Symposium in summer 2020.